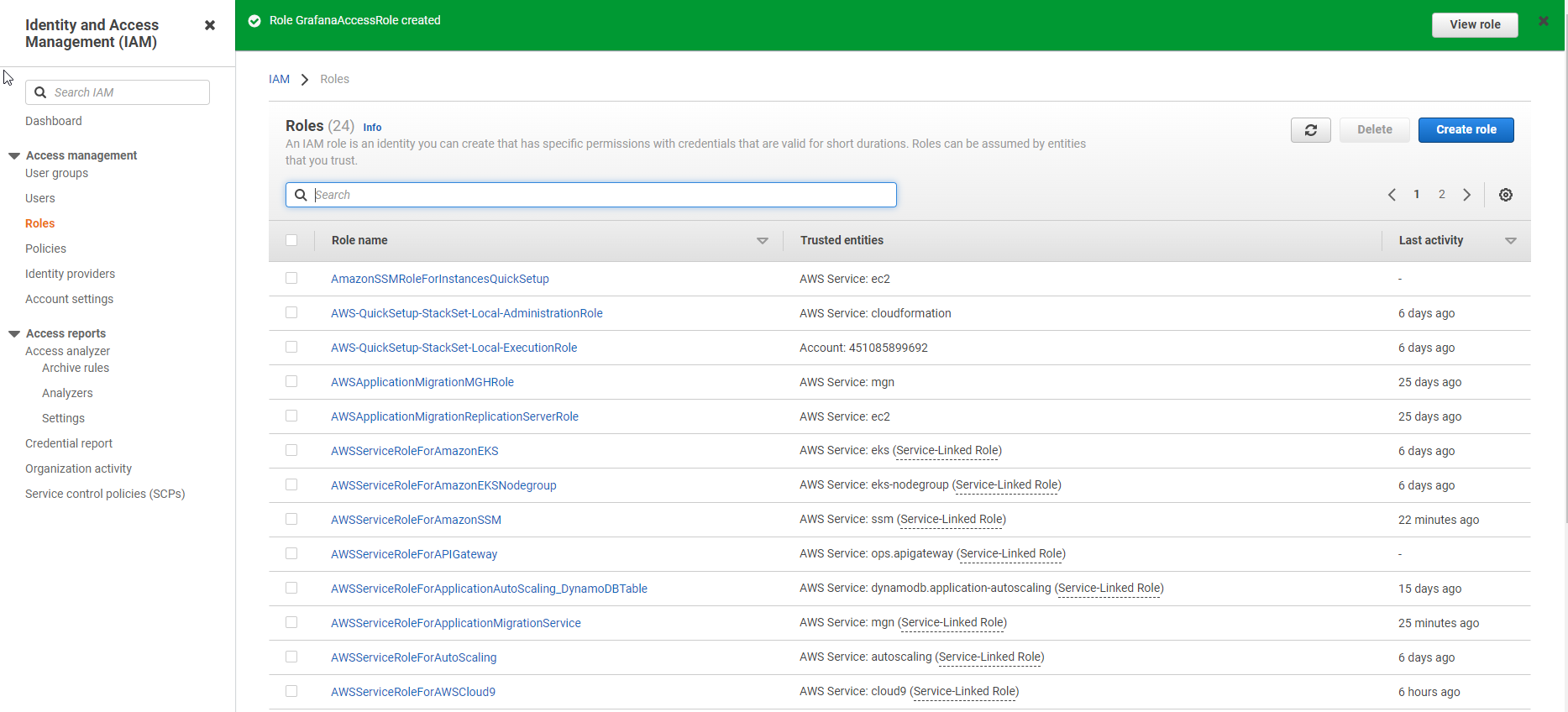
Create IAM Role
- Go to AWS Management Console
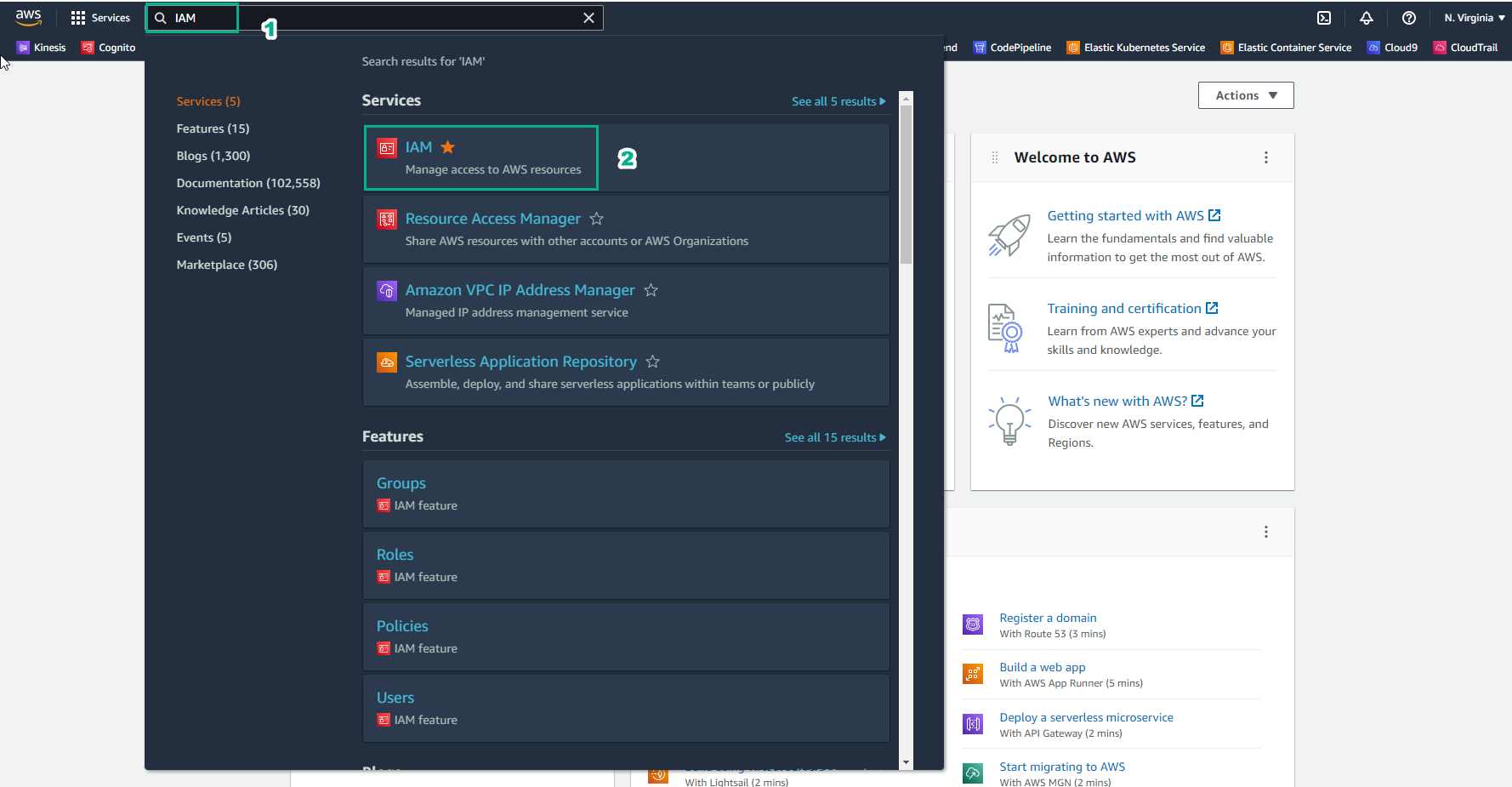
- In the IAM interface
- Select Policies
- Select Create policies
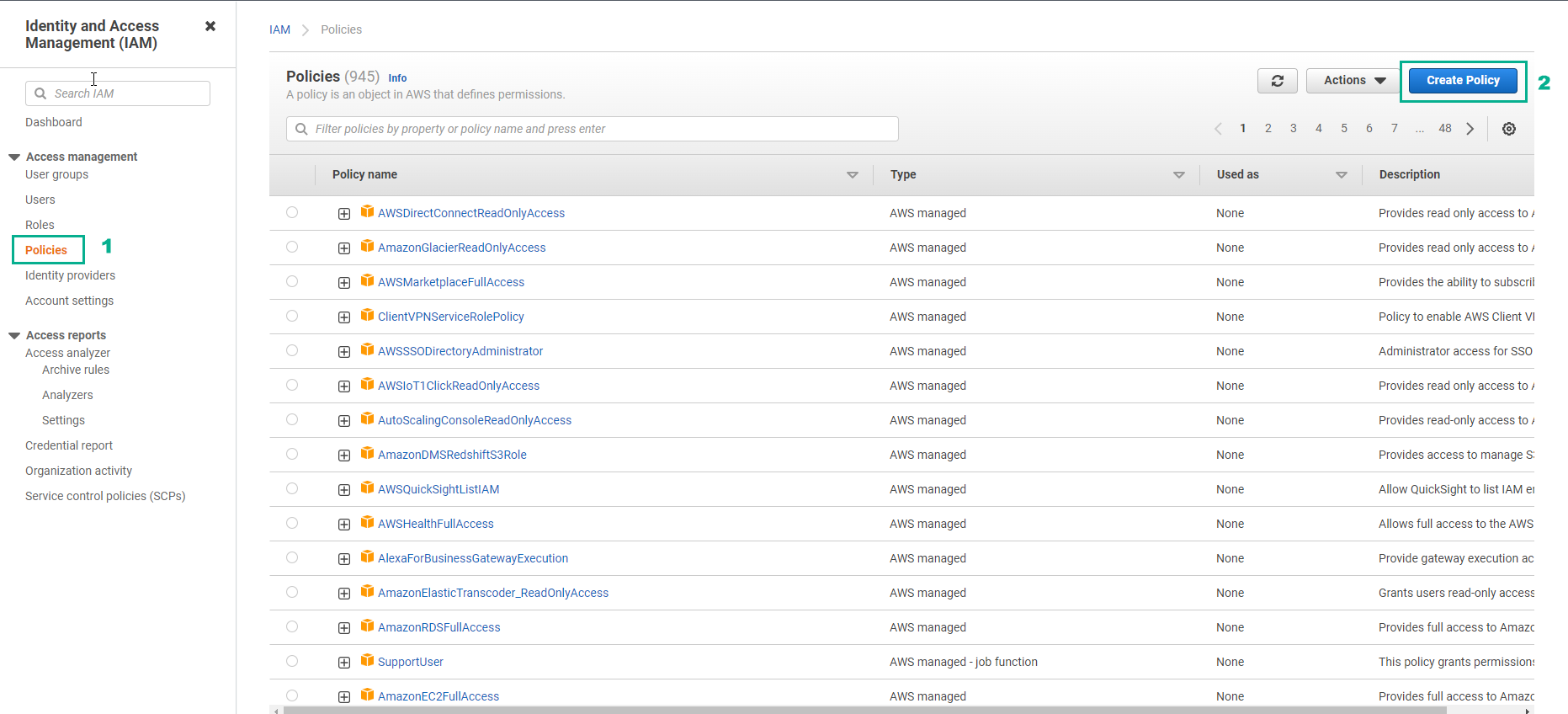
- In the Create policies interface
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowReadingMetricsFromCloudWatch",
"Effect": "Allow",
"Action": [
"cloudwatch:DescribeAlarmsForMetric",
"cloudwatch:ListMetrics",
"cloudwatch:GetMetricStatistics",
"cloudwatch:GetMetricData"
],
"Resource": "*"
},
{
"Sid": "AllowReadingTagsInstancesRegionsFromEC2",
"Effect": "Allow",
"Action": ["ec2:DescribeTags", "ec2:DescribeInstances", "ec2:DescribeRegions"],
"Resource": "*"
},
{
"Sid": "AllowReadingResourcesForTags",
"Effect": "Allow",
"Action": "tag:GetResources",
"Resource": "*"
}
]
}
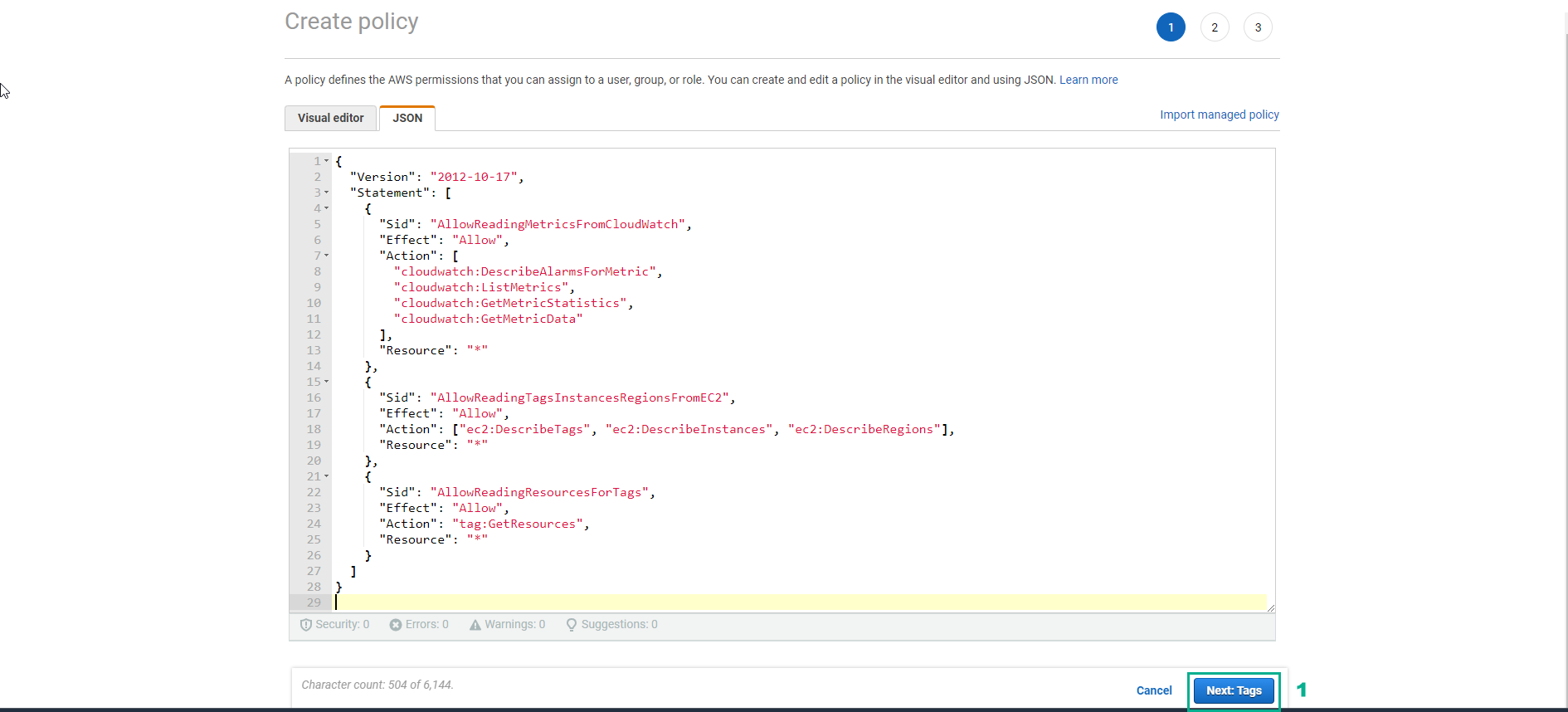
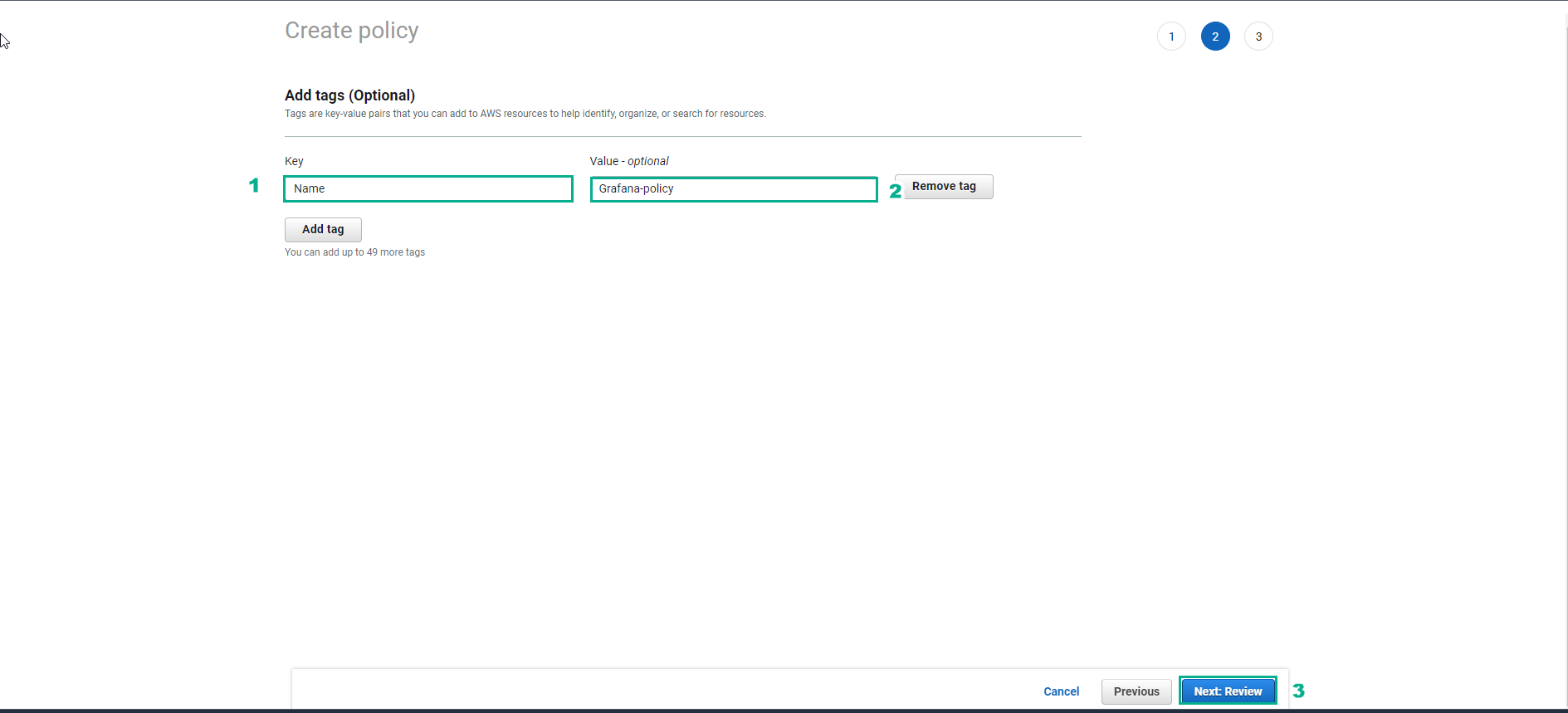
- In the Create policy interface
- Enter key value
- Enter the value value
- Select Next:Review
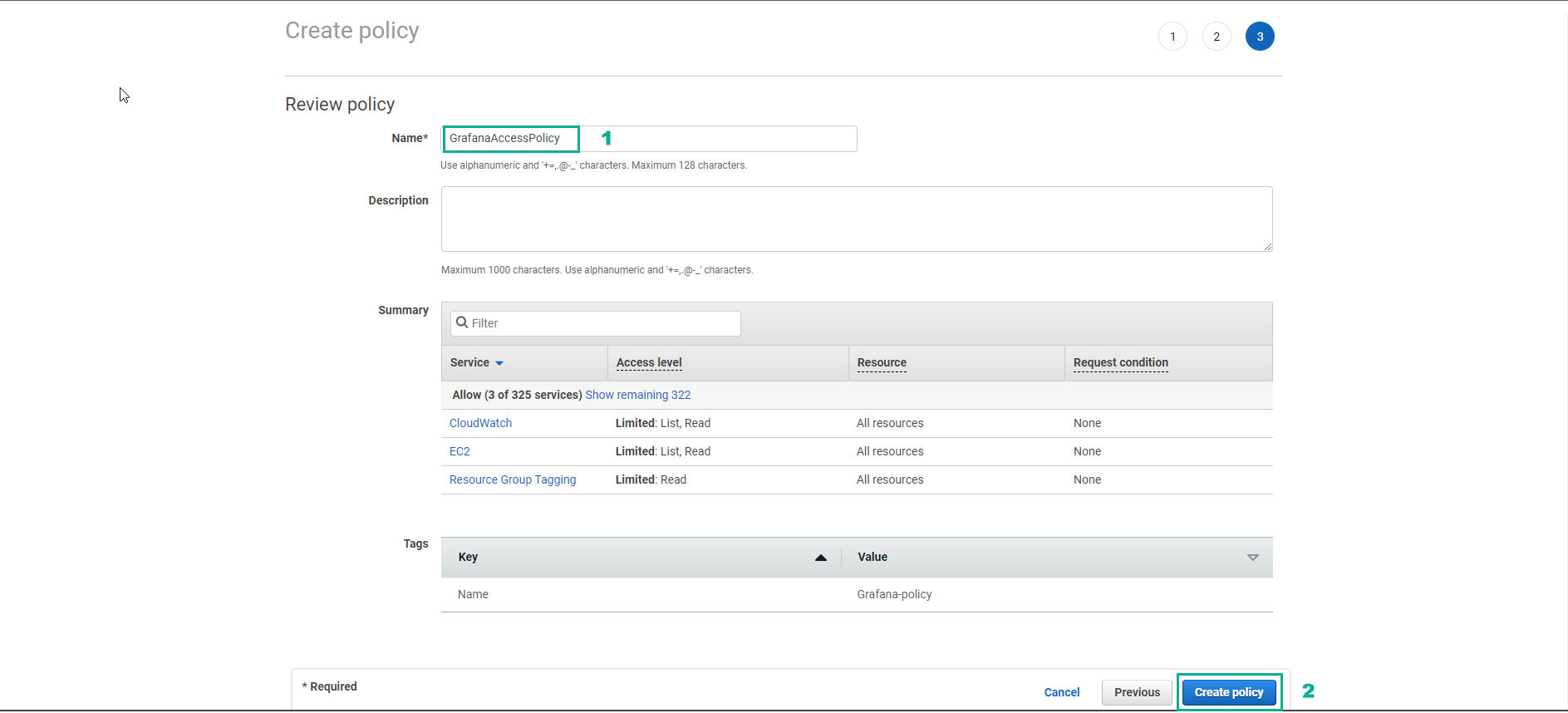
- In the Create policy interface
- Name, enter
GrafanaAccessPolicy
- Select Create policy
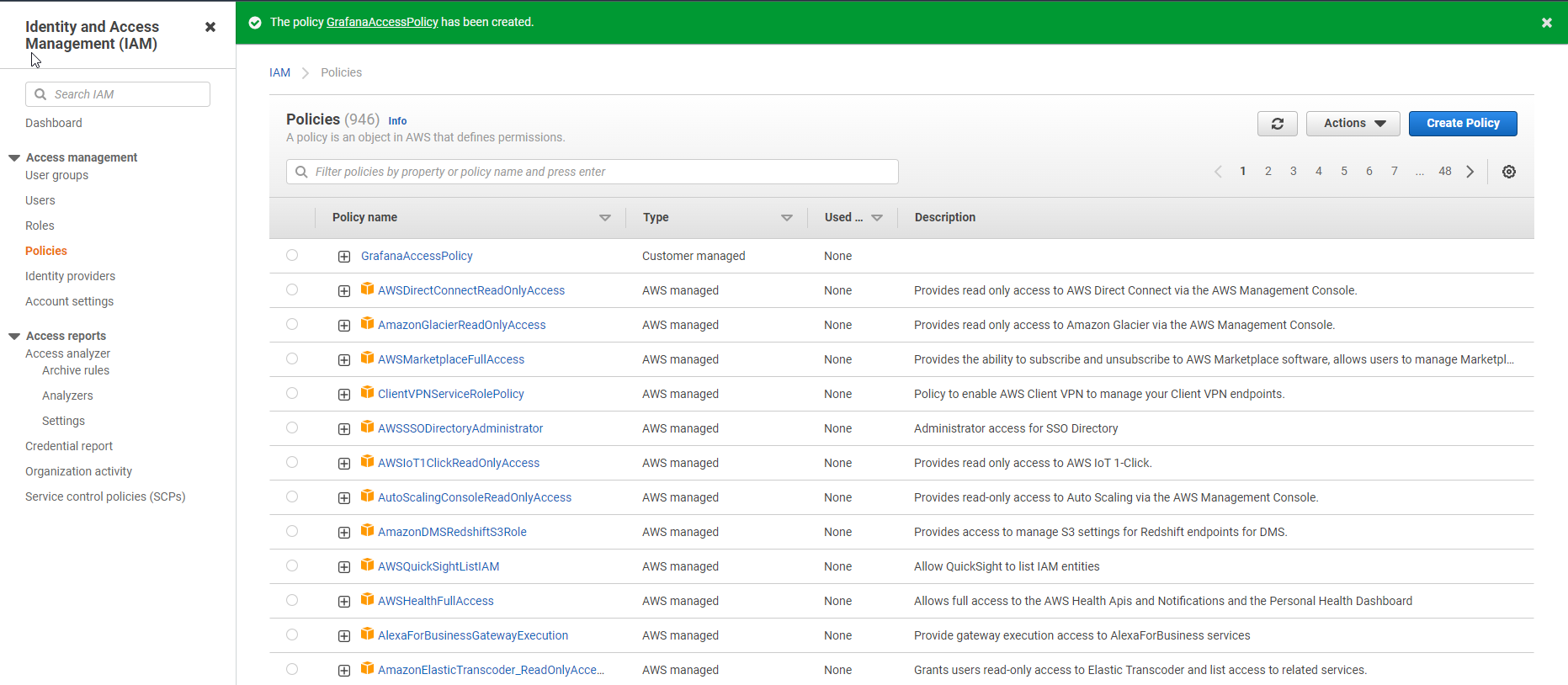
- So we have created a policy for Role successfully
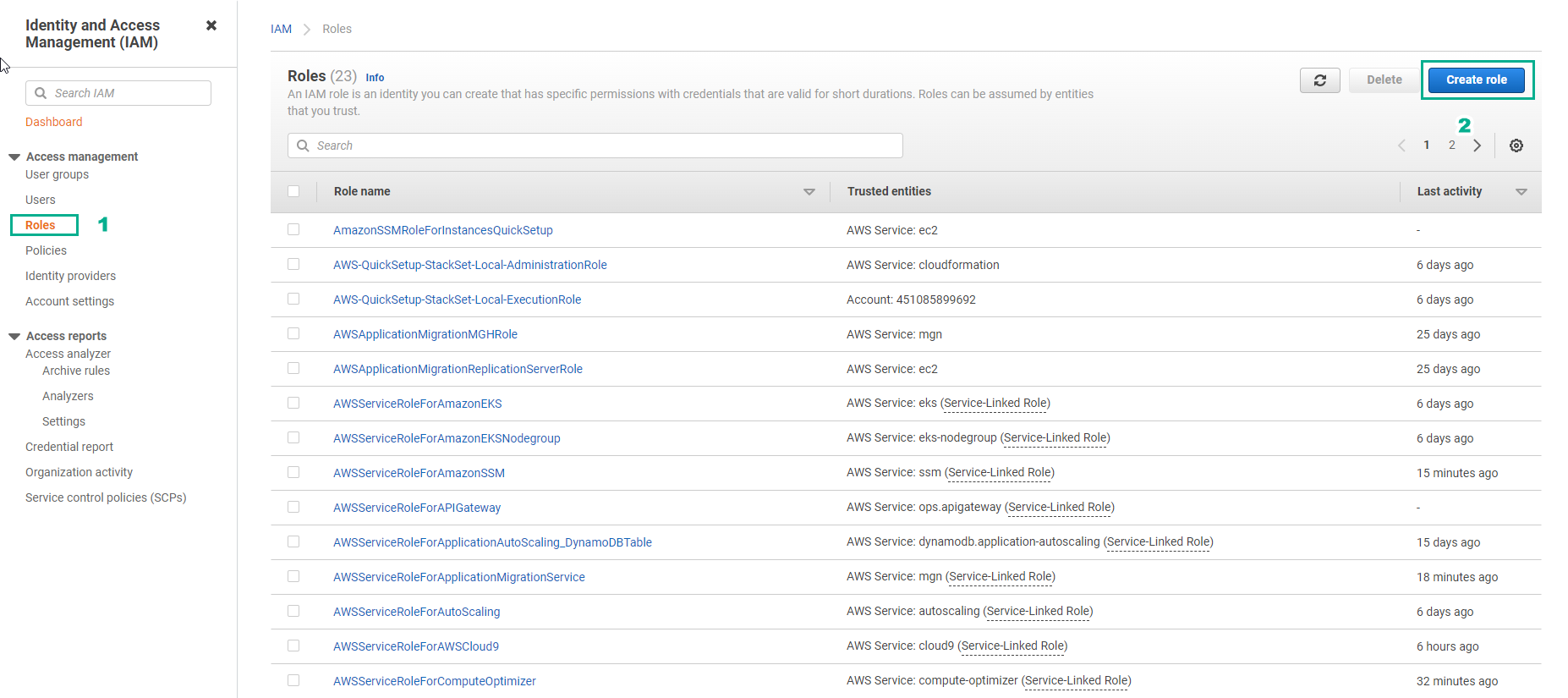
- In the IAM interface
- Select Roles
- Select Create role
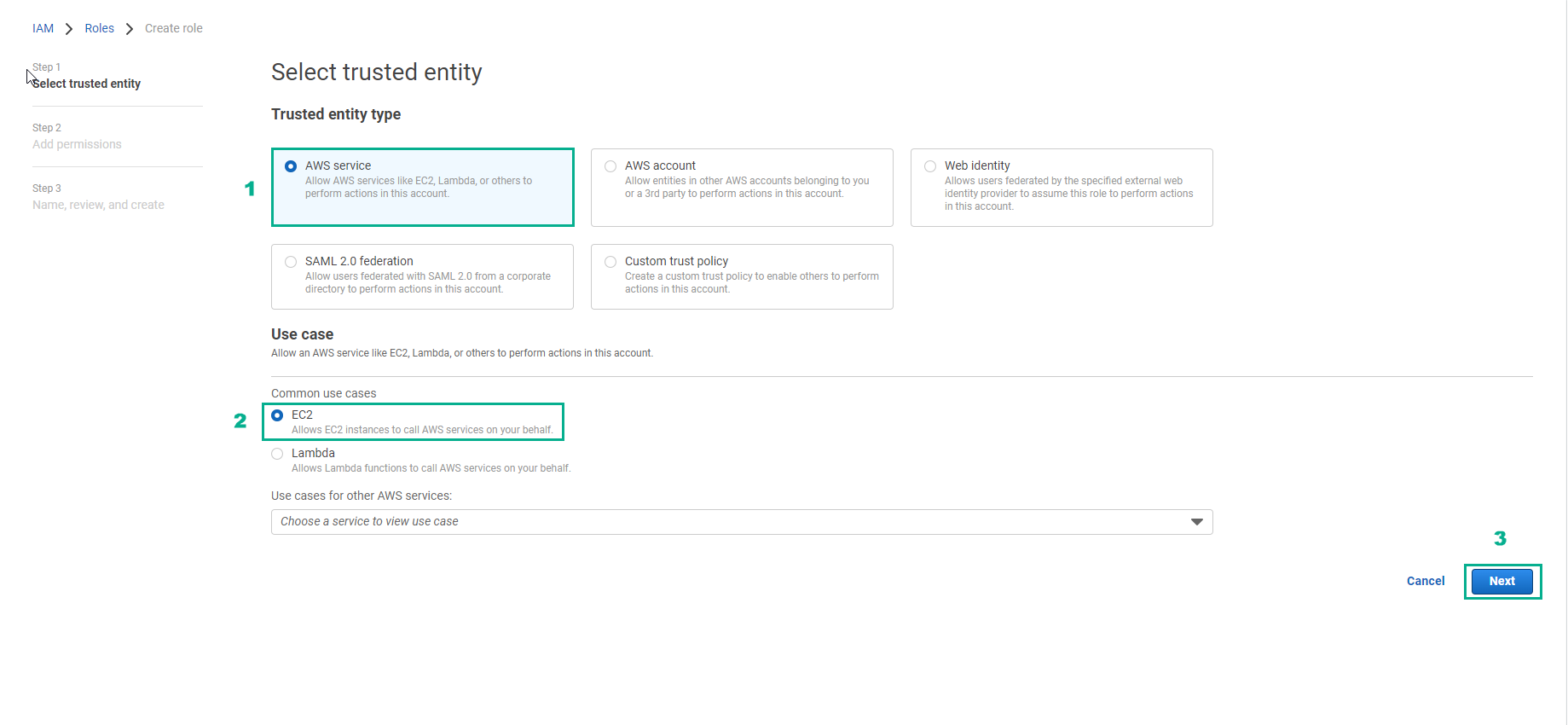
- In the Select trusted entity interface
- Select AWS service
- Select EC2
- Select Next
- In the Add permissions interface
- Find and select GrafanaAccessPolicy
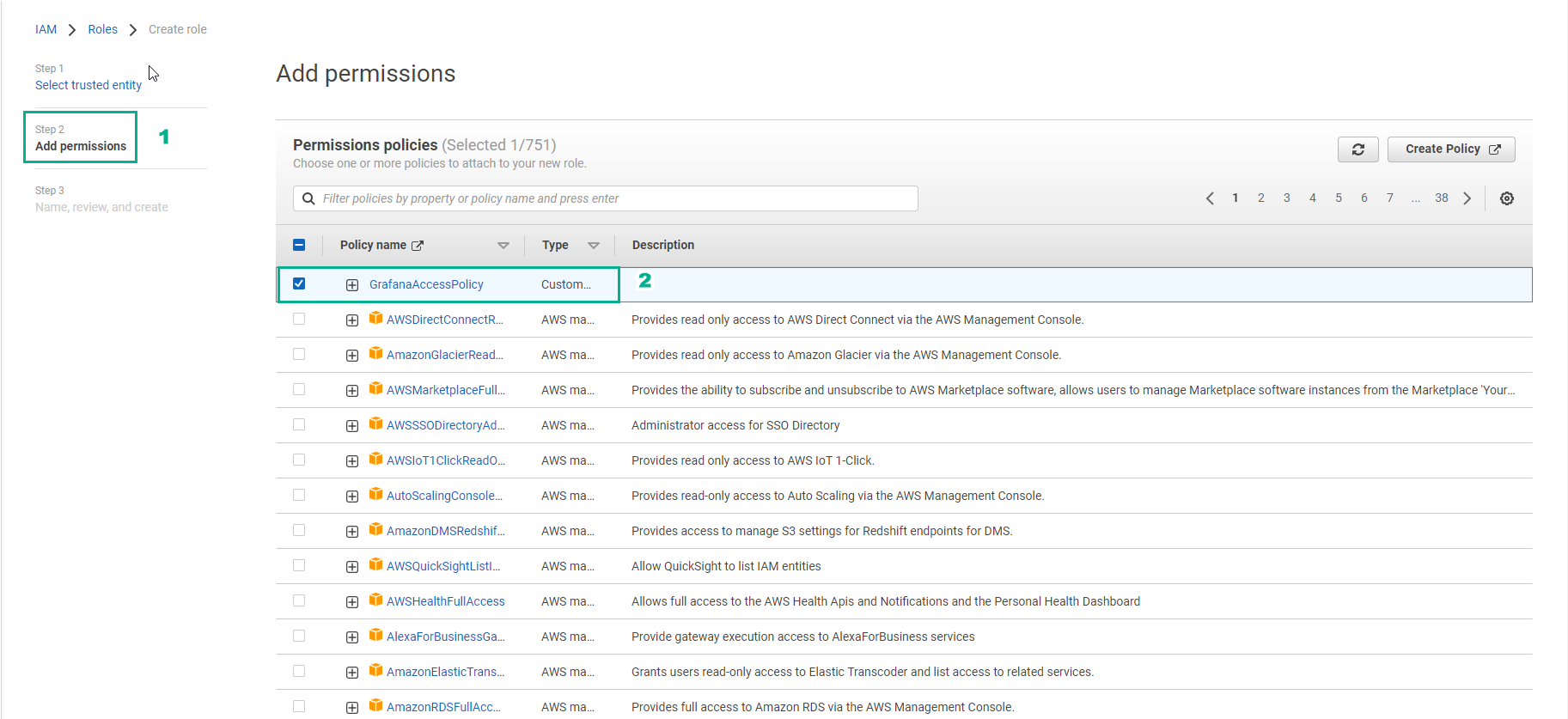
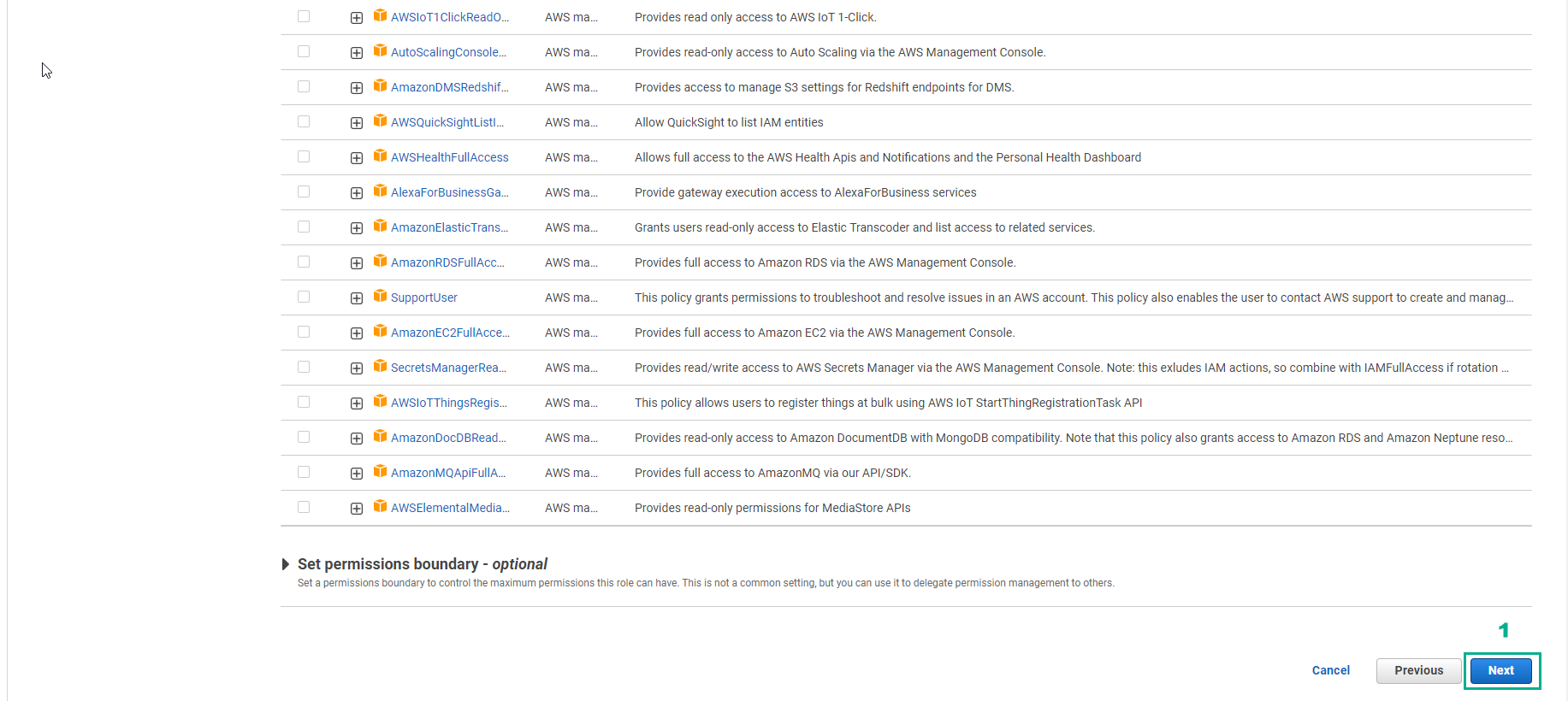
- Select Next
- In Name, review and create step
- Role name, enter ```GrafanaAccessRole````
- Description, enter
Role for Grafana Access
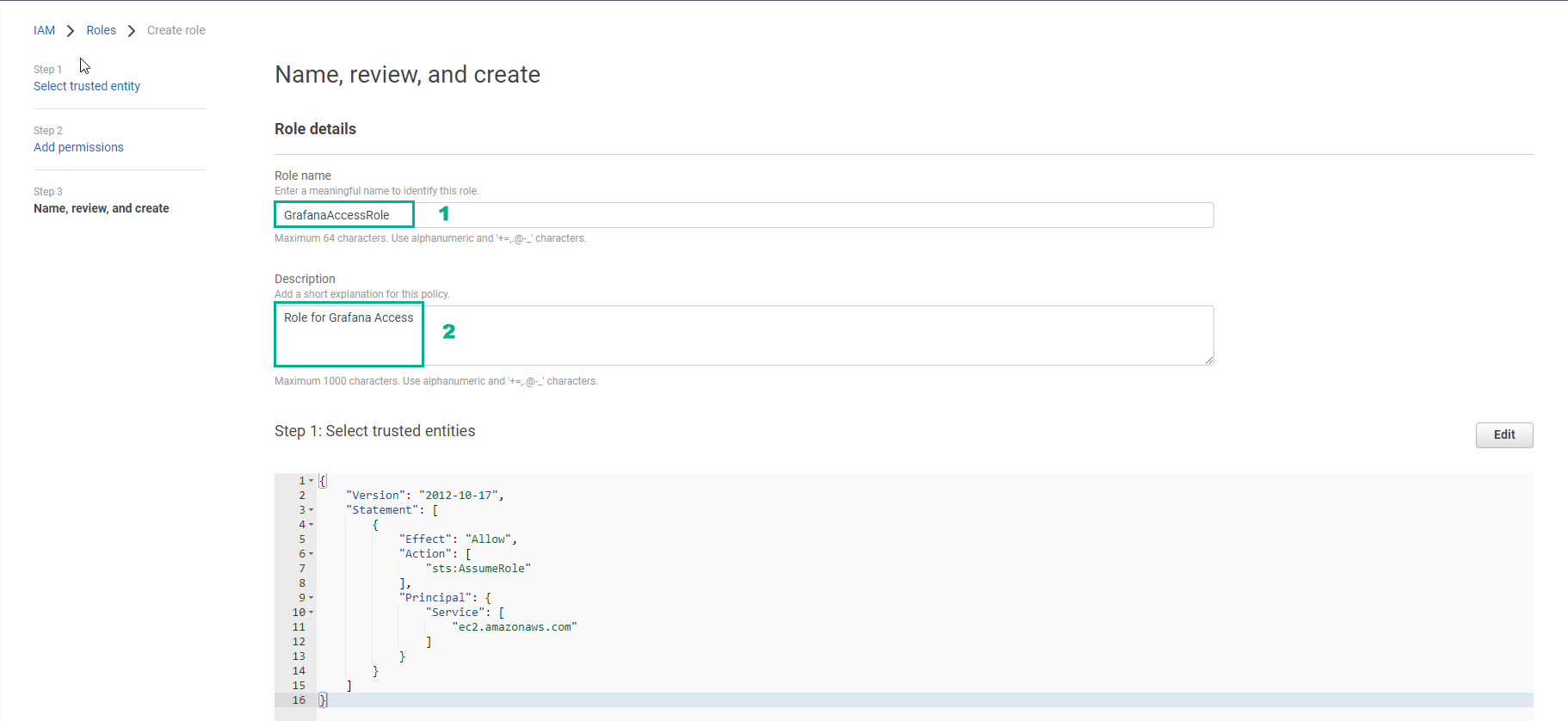
- Select Create role
- Complete role creation for EC2 instance